Single Sign-On (SSO) simplifies authentication by allowing users to access multiple applications with one set of credentials. However, when issues arise, they can disrupt workflows and frustrate users and administrators.
In Jotform, we identify a set of common SSO challenges. It could be a login failure, misconfigured settings, security issues, etc. Addressing these common issues gives you insights into maintaining a seamless and secure user experience in your Jotform Enterprise Server. Let’s get started!
Issues During Setting Up SSO
Misconfiguring your SSO can block user access, expose security vulnerabilities, disrupt workflows, cause login loops, flood systems with errors, and violate compliance policies. Addressing these issues can restore functionality, enhance security, and ensure compliance, minimizing disruption to your organization.
Identifier Settings Mismatch
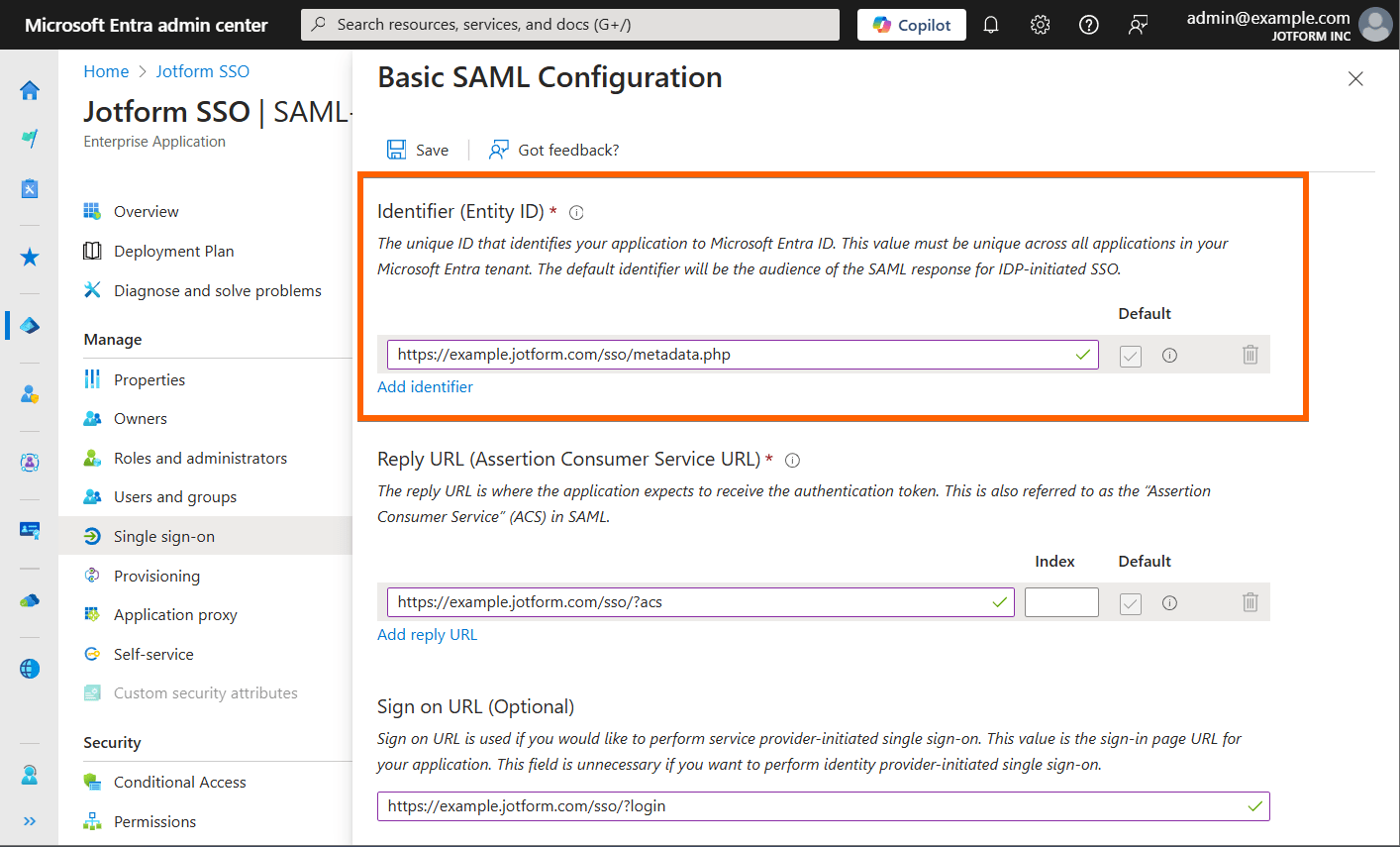
This problem is related to your Identifier (Entity ID) settings. In this case, you won’t be able to activate SSO when you input the SAML configuration without specifying the protocol (such as “https://“) at the beginning of the URL.
Here’s an example of a correct SAML Configuration with Microsoft Entra SSO:
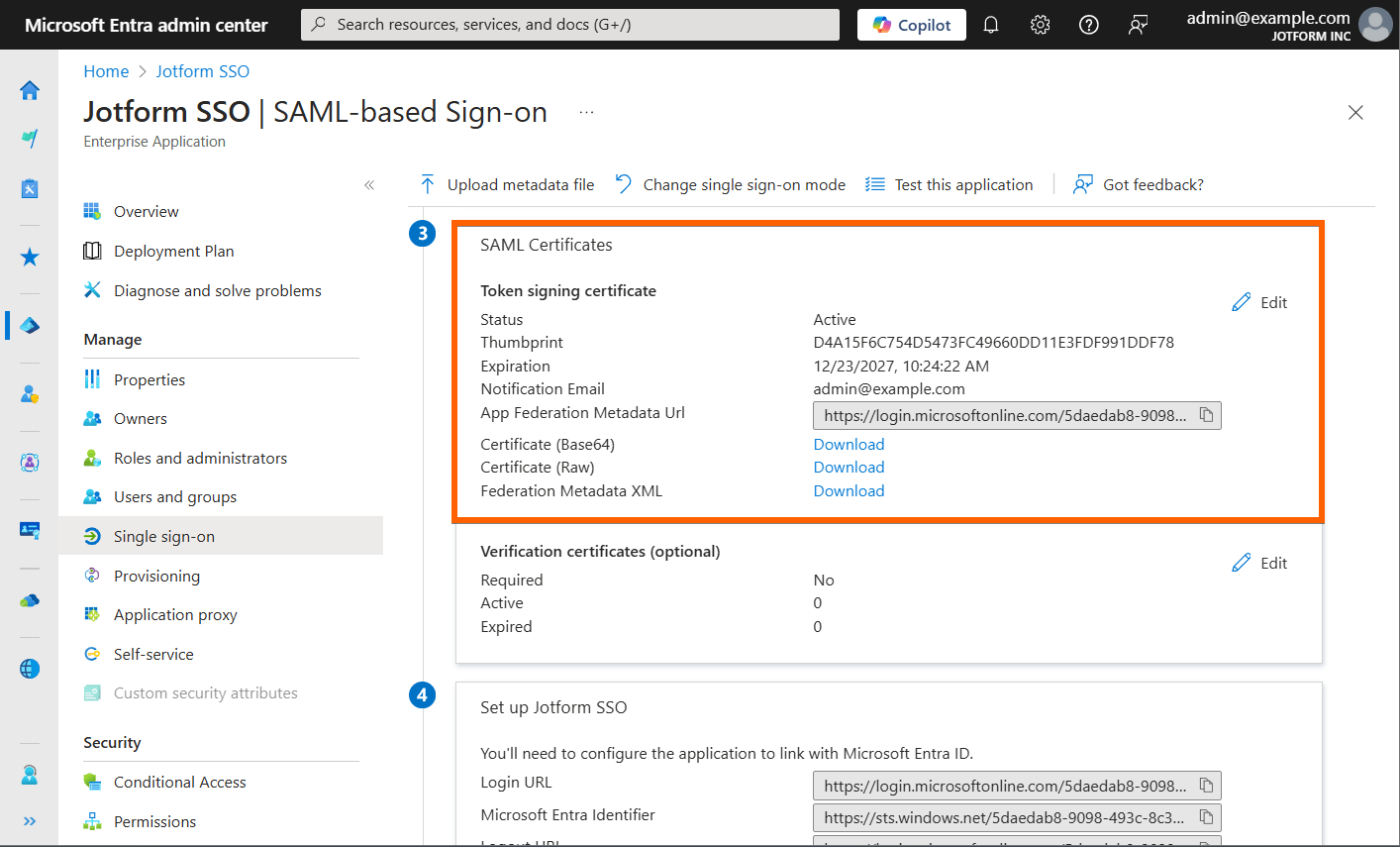
Certificate Expired
There are two distinct types of certificates involved in the SSO authentication process. Jotform provides one, and the other is provided by the Identity Provider (IdP). When you encounter an Expired Certificate error, it is typically the certificate from the IdP provider. Here’s an example of Microsoft Entra SSO SAML Certificates:
You should generate a new certificate if your IdP provider does not renew it automatically. Next, go to your SSO settings through your Jotform Enterprise Admin Console to paste the newly acquired certificate into the designated certificate section. The reason for focusing on the IdP-provided certificate is that if the certificate we issued expires, you should still be able to log in to your Jotform Enterprise Server to create a support ticket.
SSO Email Not Found
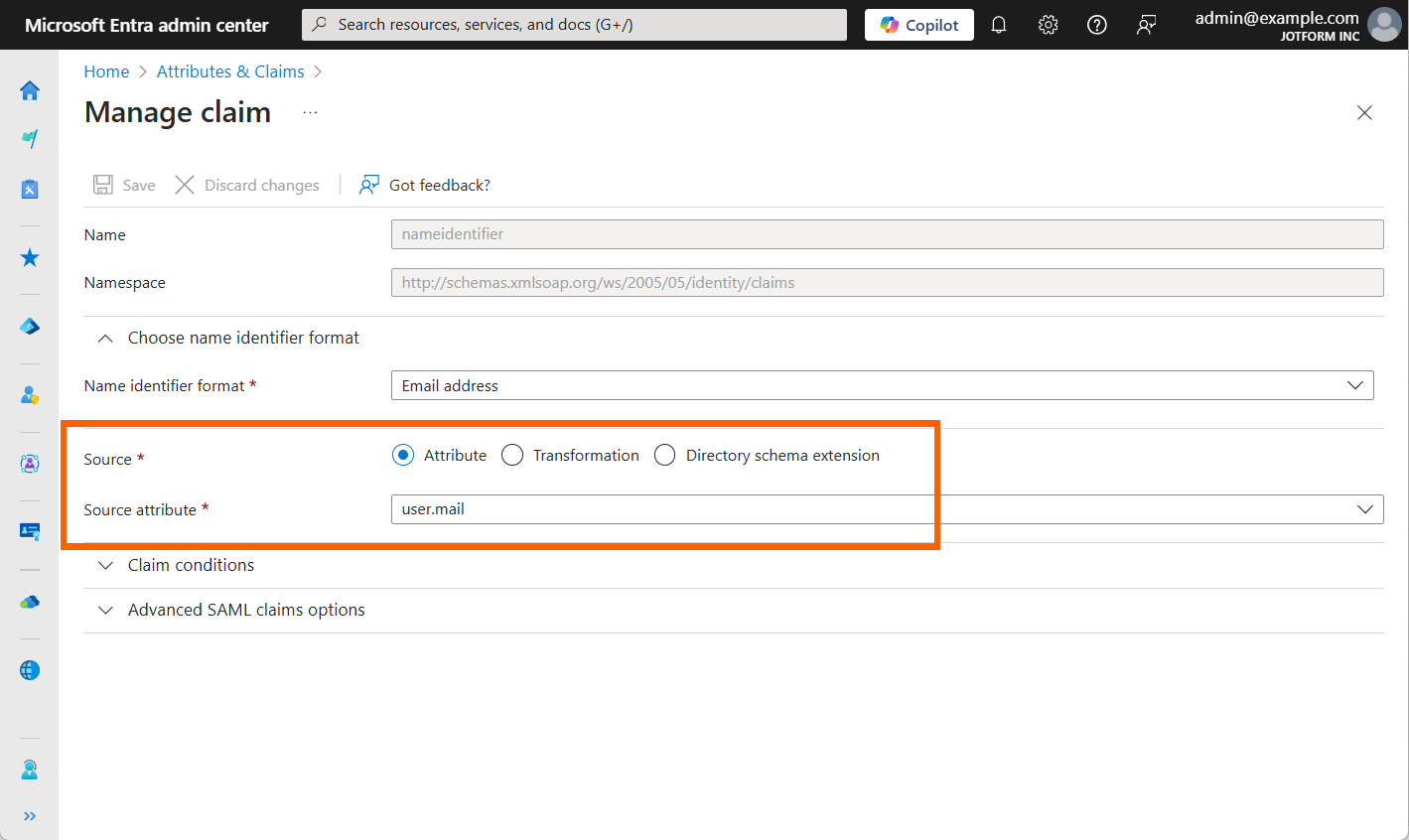
An email address is required when adding a user to your Identity Provider (IdP) for Jotform’s Single Sign-On (SSO) functionality. This email address acts as the primary identifier, enabling Jotform to authenticate and recognize the user effectively.
You have the flexibility to either include the email address within the Name ID format or add a separate claim specifically for the email. Regardless of the chosen method, every user account must be associated with a valid email address.
Here’s an example of the Microsoft Entra SSO’s Unique User Identifier (Name ID), which points to the email address:
Note
The error, as indicated, can also lead to unexpected logout sessions for users who are already logged in. This issue is anticipated to be resolved once the necessary modifications with the Name ID are implemented in the IdP.
Issues During Logging Out with SSO Enabled
Single Sign-On (SSO) simplifies login across multiple applications but can complicate logging out due to challenges in synchronizing session termination across systems. Addressing these issues is essential for ensuring security and a seamless user experience.
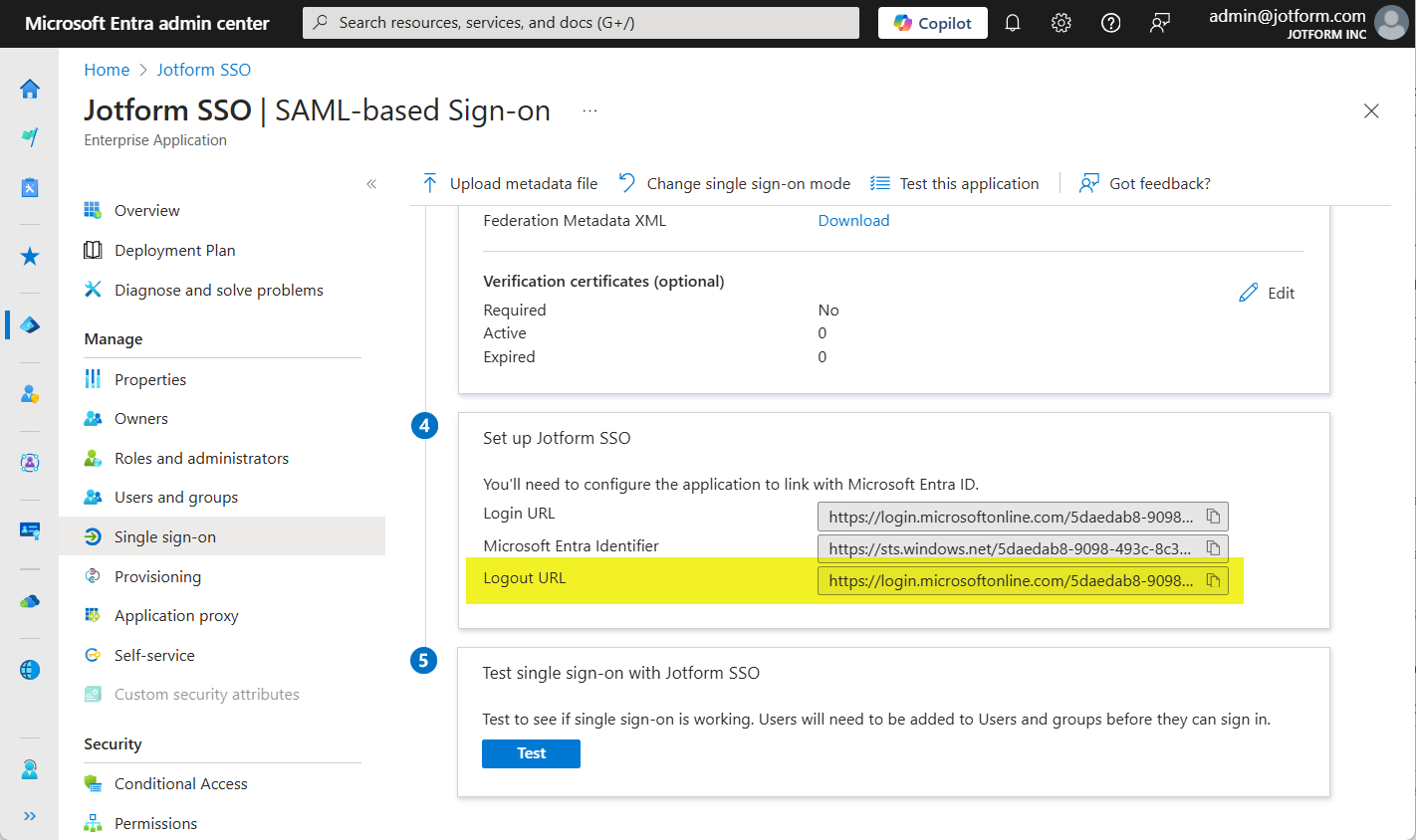
Wrong SLO URL
A wrong SLO URL occurs when you enter an incorrect Single Logout (SLO) URL in the SSO settings of your Jotform Enterprise Server. This misconfiguration can cause a loop, repeatedly redirecting Enterprise users without successfully logging them out.
The SLO URL is typically identical to the SSO URL. You can conveniently access this URL from the Single Sign-On panel within your account settings. Here’s an example of an SSLO URL from Microsoft Entra:
SLO URL Not Found – Google SSO
Most IdPs support SLO, but this is not a feature Google SSO offers. In such cases, you should leave the SLO URL in your Jotform Enterprise server blank. Next, contact Enterprise Support to have your Enterprise server set up with a logout page that would look like the following:
Issues During Logging In with SSO Enabled
Logging in to an SSO-enabled Jotform Enterprise Server can sometimes present challenges that disrupt user access. These issues often stem from misconfigurations related to SLO URLs. Resolving these problems ensures a seamless login experience for your Enterprise users.
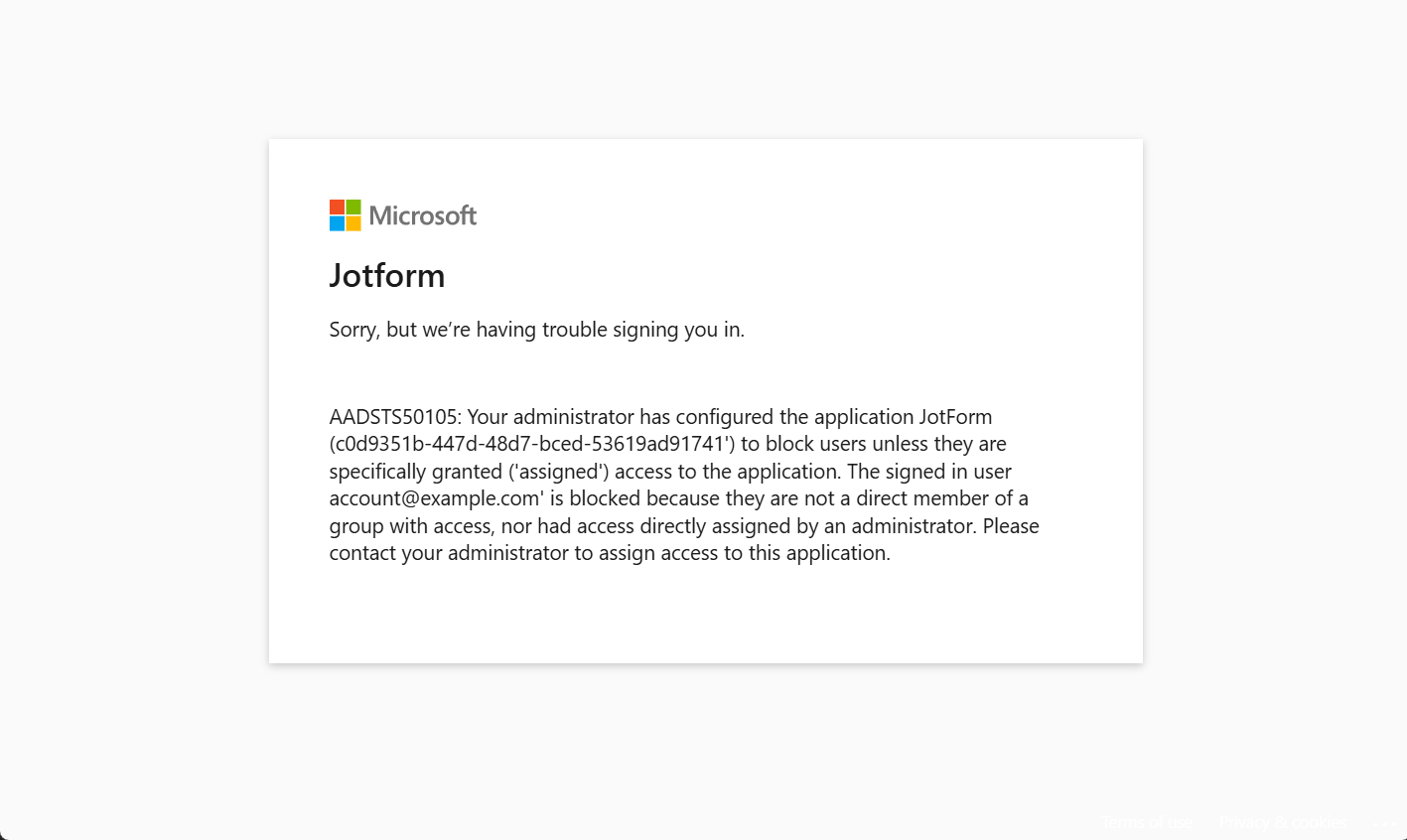
The Signed In User is Blocked
Enabling SSO requires more than just adding users to your Enterprise Server. You must also ensure that you add them appropriately to your SSO provider. If you skip this step, your new users cannot log in successfully. Below is an example of the error message users may encounter if you do not add them to your SSO provider:
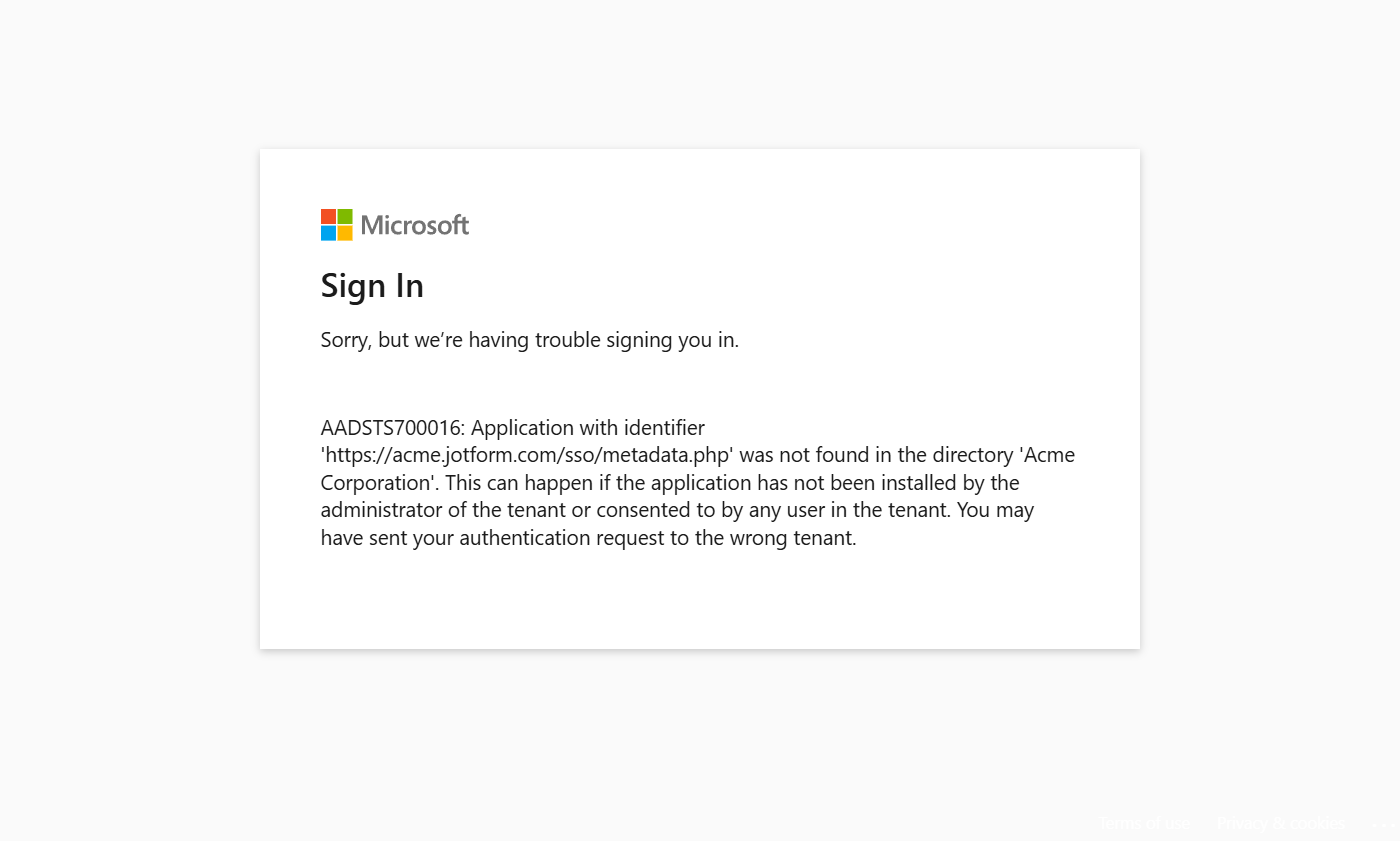
Application With Identifier Was Not Found
If your Enterprise Users see an error stating that metadata information is missing from the directory, it typically means you incorrectly entered the metadata in the Admin Console. This issue often arises during SSO setup or after changes to the domain or slug.
To resolve it, you must disable SSO before updating the custom domain and then reconfigure the metadata in the SSO settings after enabling it.
Note
We are working on enhancing this experience with Jotform Enterprise. In the meantime, if you update your domain or slug while SSO is enabled on your server, access may become unavailable. Please contact Enterprise Support for assistance.
Issues Related to SSO Attributes
Single Sign-On (SSO) makes it easier to access multiple applications with one login, but missing or incorrect attributes can cause login issues and complicate managing enterprise forms. Setting up SSO attributes correctly is key to providing a smooth user experience and keeping systems running efficiently.
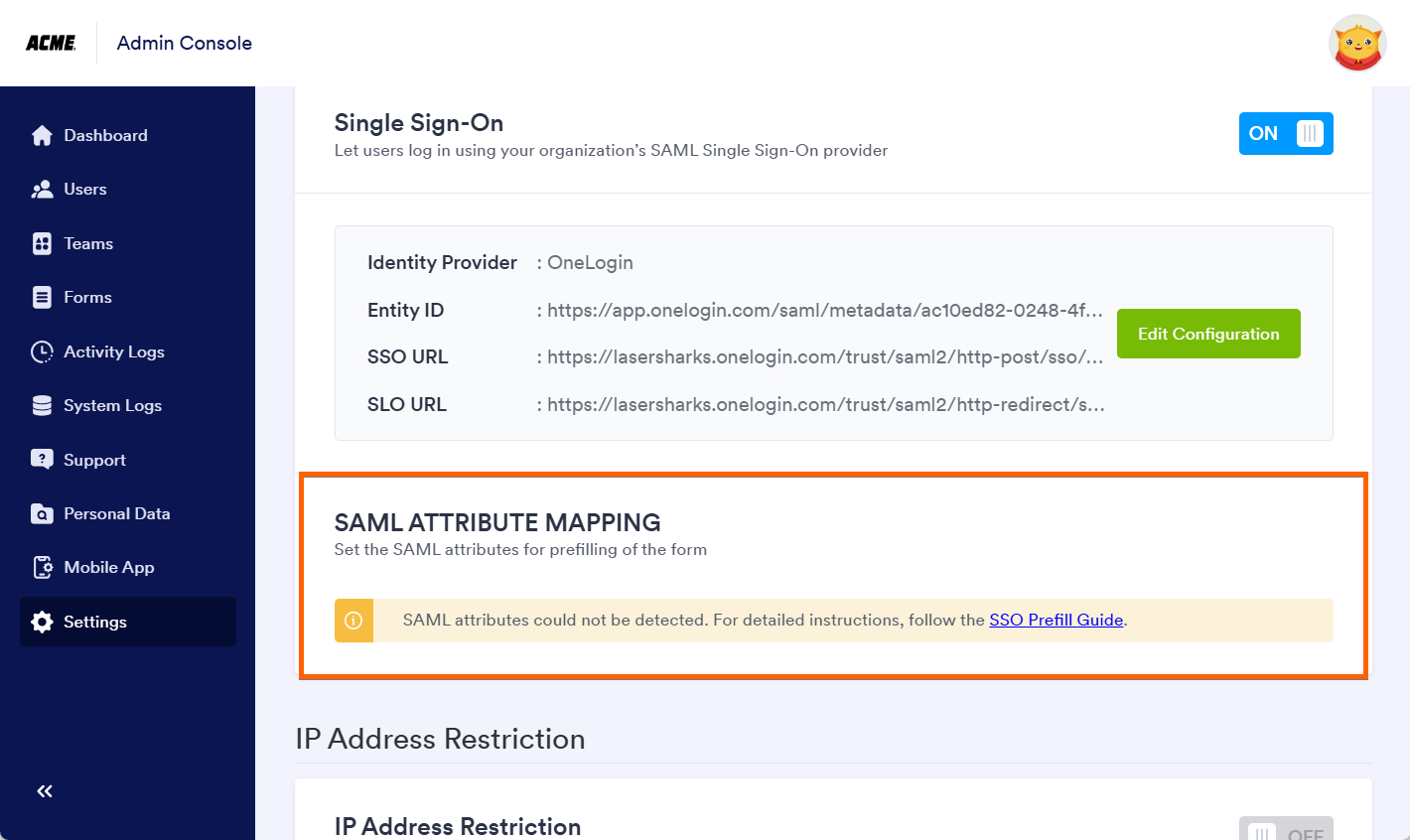
Attribute Mapping Requests
With Jotform Enterprise, mapping your SAML attributes is possible through your Enterprise Server settings. If the system cannot detect the SAML attributes, you’ll see it as a warning through the settings page, as shown in the image below:
To fix this, you must set up SSO Prefill as outlined. Visit How to Enable SSO Prefill for more details.
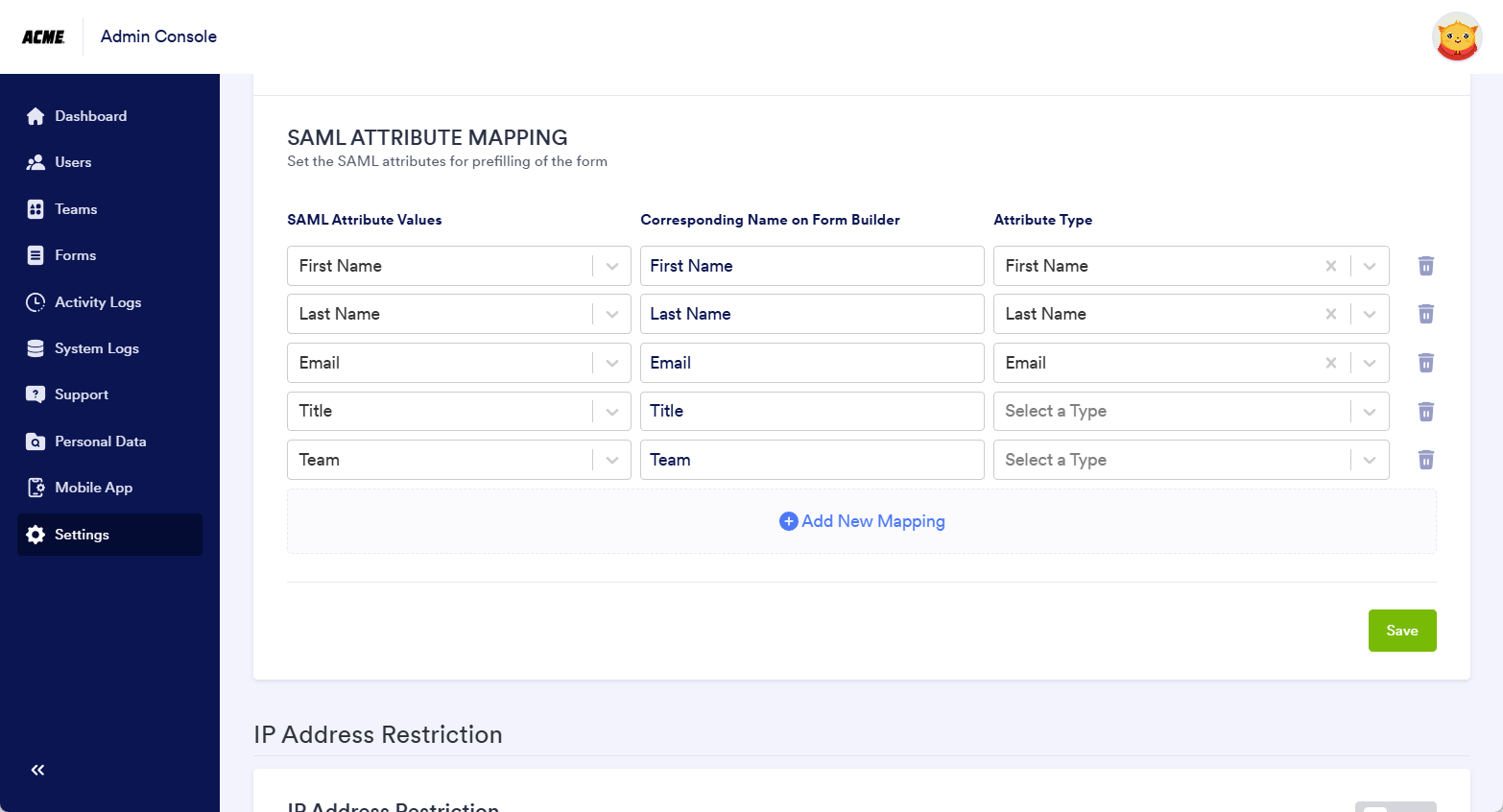
Adding SAML Attribute Types
The available Attribute Types are specifically designed for the first name, last name, and email in Jotform Enterprise. However, you can add more mapping without selecting from the Attribute Type as long as you input both SAML Attribute Values and Corresponding Name on Form Builder fields. Here’s an example of the SAML Attribute Mapping:
Attributes not Appearing in Attribute Mapping
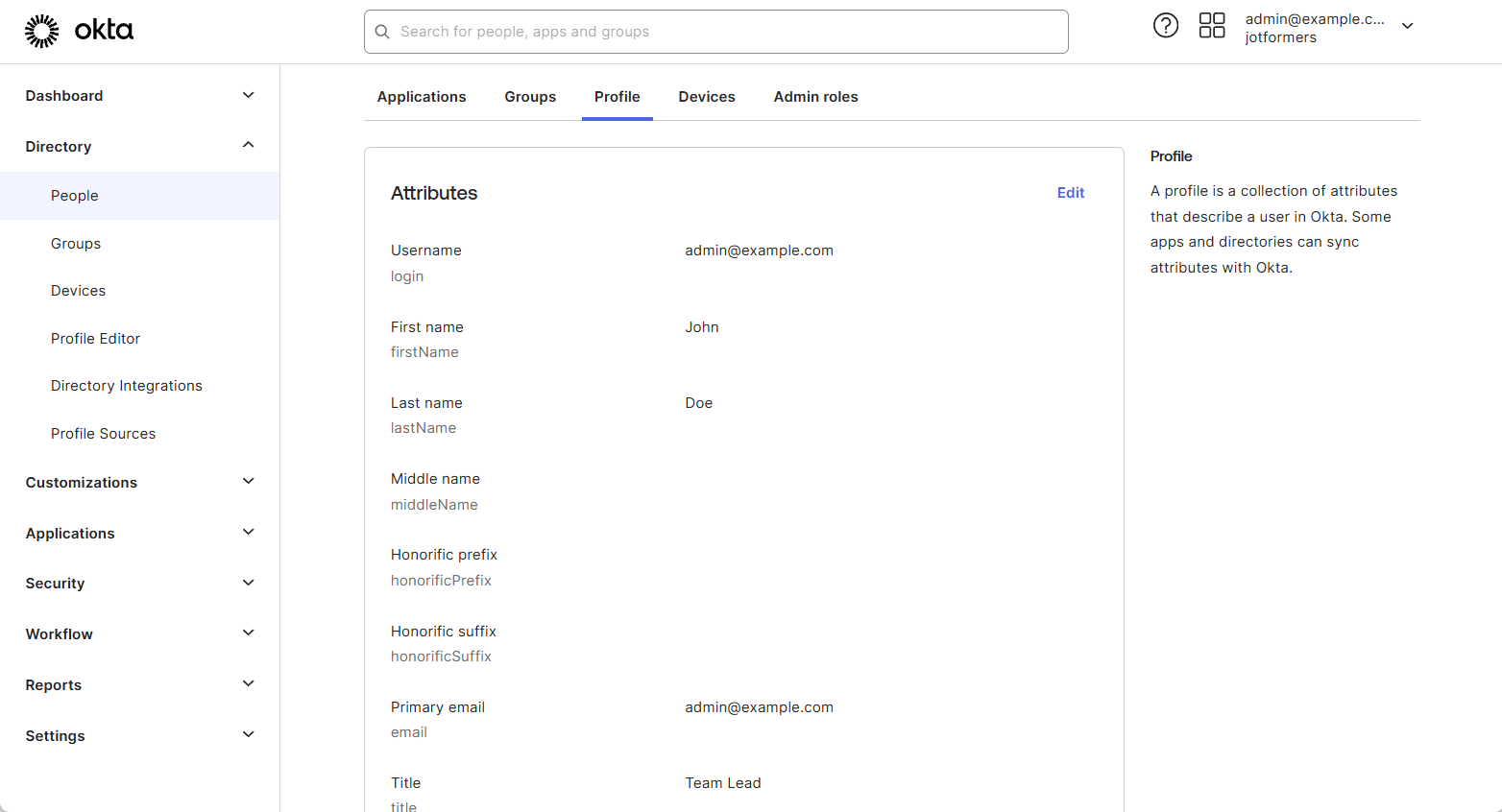
Identity Providers (IdP) offer a wide range of attributes you can claim. Here’s an example of attributes available from Okta:
To ensure an attribute added to your IdP appears in the Admin Console, you must provide a corresponding value for that attribute. Any attributes without a value won’t appear in your SSO settings within your Jotform Enterprise Server.
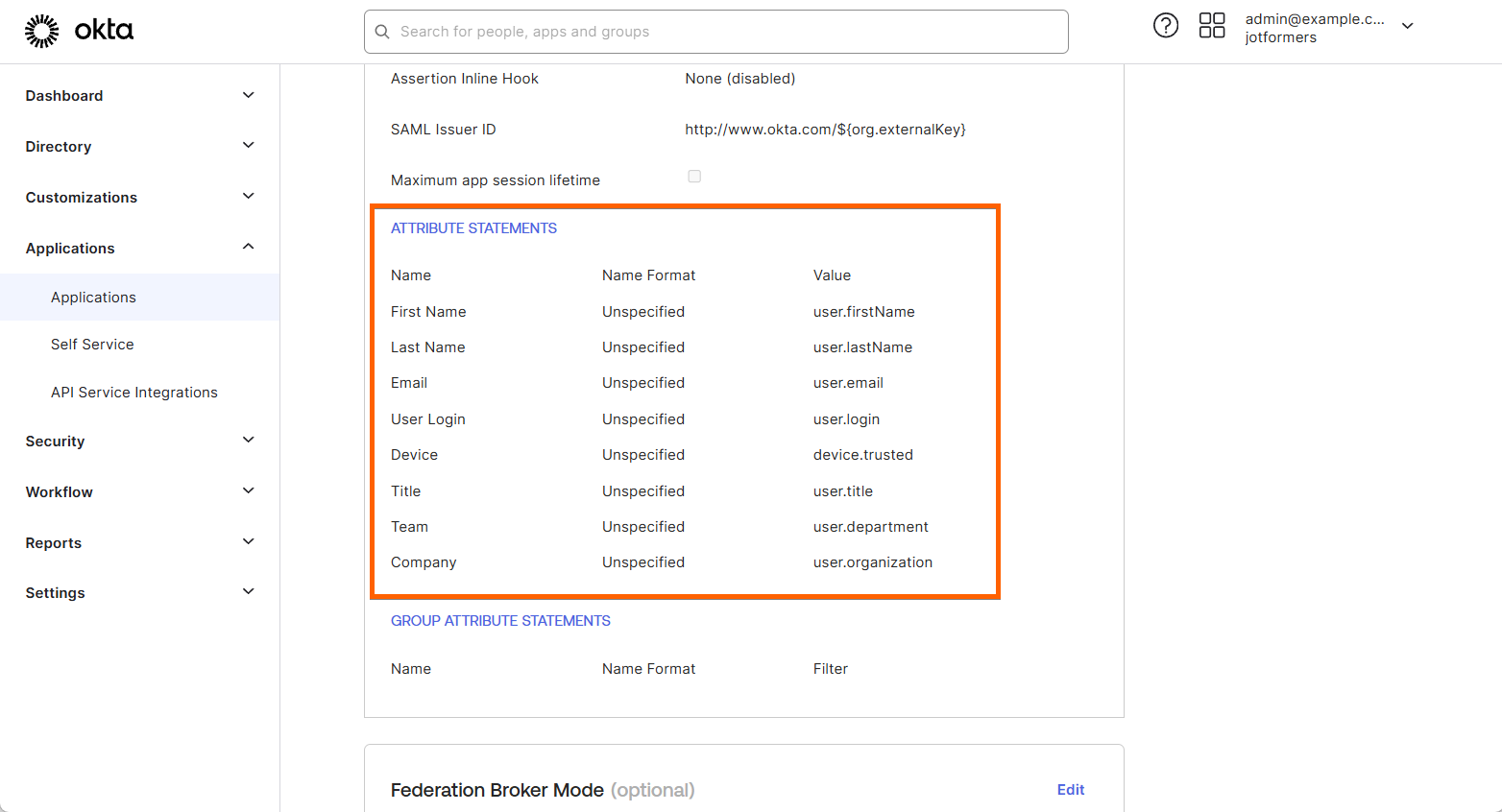
Lastly, you must also add these attributes correctly to your SSO application. Here’s an example from Okta:
Note
After you enter the attribute values in the Admin Console, you may need to log out and log back in to ensure the updated attributes are applied during the subsequent SSO process. This step is necessary because the system retrieves attribute values during login.


Send Comment: